Hey there, fellow business owners! Today, we have some important news to share with you about the recent cyberattack on Seiko, one of the world’s largest and most renowned watchmakers. You might be thinking, “Why should I care about this?” Well, my friend, this incident serves as a wake-up call for all of us. It’s a reminder that no company, big or small, is immune to the ever-growing threat of cybercrime.
Seiko recently disclosed a data breach that occurred when an unauthorized third party gained access to their IT infrastructure and stole sensitive information. This breach not only puts Seiko’s reputation at risk but also highlights the importance of cybersecurity for businesses like yours and mine. Let’s dive deeper into the details and understand the implications.
The Breach and Seiko’s Response
On August 10th, 2023, Seiko released a statement informing the public about the unauthorized access to their servers. They revealed that an unidentified party had breached their systems, potentially compromising valuable data. Imagine someone breaking into your office and rummaging through your confidential files—it’s a chilling thought, isn’t it?
Seiko took immediate action and enlisted the help of external cybersecurity experts to investigate the breach. Unfortunately, their worst fears were confirmed—there had indeed been a breach, and sensitive information may have been compromised. They promptly apologized to their customers and business partners who might be affected, urging them to stay vigilant against any suspicious emails or communications impersonating Seiko.
The Culprit Revealed: BlackCat Ransomware Gang
Now, here’s where things get really interesting. The BlackCat ransomware group has come forward, claiming responsibility for the attack on Seiko. They even posted samples of the stolen data as proof. These cybercriminals didn’t just stop there—they went on to taunt Seiko about their IT security and leaked confidential information, such as production plans, employee passport scans, and even watch designs!
Just imagine if your business’s secrets were exposed to your competitors or the world. It’s like handing them a roadmap to replicate your success. This is the harsh reality that Seiko now faces. And it’s a stark reminder of the need for robust cybersecurity measures to protect our businesses from such devastating breaches.

Source: BleepingComputer
BlackCat is no ordinary cybercriminal gang—they are notorious for their advanced ransomware tactics. In fact, they were the first to create a dedicated website on the clearweb to leak data for specific victims. And if that wasn’t enough, they recently developed a data leak API, making it even easier for them to distribute stolen information.
Update 8/21/23: After the publication of this story, researchers at Curated Intel revealed that an initial access broker (IAB) was selling access to a Japanese manufacturing company just one day before Seiko’s breach. While the company’s name was not disclosed, the description perfectly matches Seiko’s profile, including revenue details. This raises serious concerns about the interconnectedness of cybercriminal activities and the need for proactive cybersecurity measures.
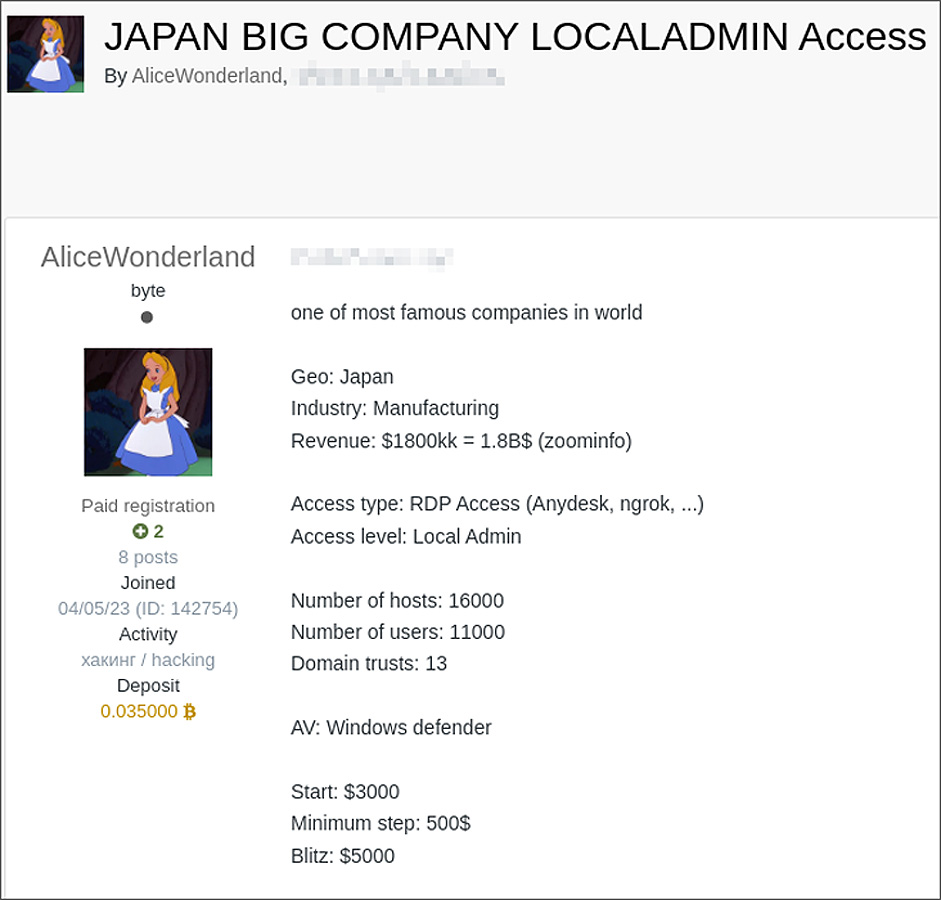
Source: Curated Intel
It’s clear that cybercriminals like BlackCat are constantly evolving and finding new ways to exploit vulnerabilities. That’s why we must remain one step ahead and prioritize cybersecurity in our businesses.
Protect Your Business with ZZ Servers
Now that you understand the grave consequences of a cyberattack, it’s time to take action to safeguard your business. At ZZ Servers, we specialize in cybersecurity, and we’re here to help you navigate the complex world of online threats. Our team of experts will assess your IT infrastructure, identify vulnerabilities, and implement robust security measures to keep your data safe.
Remember, cybersecurity is not a luxury—it’s a necessity. Don’t wait until it’s too late. Contact us today to learn how ZZ Servers can assist you in protecting your business from the ever-looming threat of cybercrime. Together, we can build a secure digital future for your company.


